The IDNT compute instances
The IDNT compute instances are much more than just high-performance server systems.
With an IDNT compute instance, you get access to our numerous cloud services at the same time, making manual implementation of many other required additional services superfluous.
This not only increases the security and reliability of your application, but also saves the necessary resources and therefore your financial costs.
Operating Systems
We support almost all common operating systems and distributions. Whether Microsoft Windows or Linux, our team is 100% at home in both worlds and will be happy to support you with all your administration and configuration tasks. The following overview shows you the cloud services available with the respective operating system:
| Betriebssystem / Distribution |
Cluster Storage
|
Virtual Filesystem
|
Cloud Identity
|
Secure Access
|
Private Networks
|
Snapshots
|
Backup & Recovery
|
|
|---|---|---|---|---|---|---|---|---|
| Windows Server 2012 R2 | ||||||||
| Centos Linux 6.x RedHat Enterprise Linux 6.x |
||||||||
| Debian Linux Ubuntu Linux SuSE Linux |
| Supported | Currently Unavailable | Unsupported | Limited Support |
CPU & Memory
Die IDNT Compute Instanzen ermöglichen das dynamische Anpassen von CPU und Arbeitsspeicher. Sofern einer Compute Instanz mehr Ressourcen zugewiesen werden, als das Host System bereit stellen kann, erfolgt eine Verlagerung auf ein anderes Host System, welches ausreichend Ressourcen für die Anforderung verfügbar hat (IDNT betreibt grundsätzlich kein Overcommitting). Dies kann unterbrechungsfrei im laufenden Betrieb erfolgen.
Die folgende Tabelle beschreibt welche Funktionen und Ausbaustufen bei welchen Betriebssystemen verfügbar sind:
| Betriebssystem / Distribution |
RAM Minimum
|
RAM Maximum
|
CPU Cores Max
|
Live CPU Adj.
|
Live RAM Adj.
|
Reserve RAM Use
|
Reserve CPU Use
|
GPU Access
|
|
|---|---|---|---|---|---|---|---|---|---|
| Windows Server 2012 R2 | 1 GB | 256 GB | 32 | ||||||
| Centos Linux 6.x RedHat Enterprise Linux 6.x Debian Linux Ubuntu Linux SuSE Linux |
386 MB | 256 GB | 32 |
| Supported | Not Supported |
| RAM Minimum | The minimum amount of RAM required to start the instance. |
| RAM Maximum | The maximum amount of memory that can be allocated to an instance of this type. |
| CPU Cores Max | The maximum number of CPU cores that can be assigned to an instance. |
| Live CPU Adj. | Specifies whether the number of CPU cores can be changed during operation. This function also requires a corresponding support of the application software. |
| Live RAM Adj. | Specifies whether the working memory can be changed during operation. This function also requires a corresponding support of the application software. |
| Reserve RAM Use | If this function is supported and activated, the system can use additional memory of the host system that has not been reserved for other instances. However, this memory is allocated to the instance after goodwill. |
| Reserve CPU Use | If this function is supported and activated, the system can use additional CPU power of the host system, which has not been reserved for other instances. However, this CPU performance is allocated to the instance after goodwill. |
| GPU Access | Specifies whether this system has the option to perform floating point calculations on a GPU. |
Network connection
|
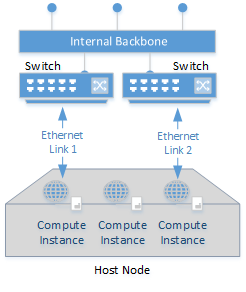
IDNT compute instances are redundantly connected with 2 x 1,10 or 40 GBit/s. Internal data transfer is free of charge within the same availability zone. The connection is made to separate Ethernet segments, so that even the failure of a network component has no influence on availability. Intelligent bandwidth management ensures that there are no bottlenecks in network availability and throughput. Application-specific bandwidth restrictions and prioritization of specific data streams can be implemented at the customer's request. |
 |
Storage
|
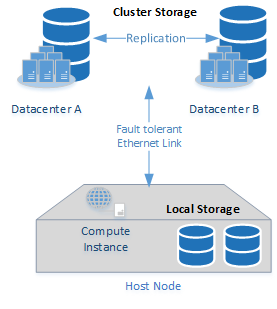
There are two different storage space variants available for all IDNT compute instances. Both storage variants are completely redundant (no single point of failure) and differ primarily in the scaling options, data throughput and access times. For smaller installations with small data volumes, only local storage is generally used. |
 |
Local Storage
The IDNT Local Storage hosts the operating system itself and provides the fastest storage space. This consists of storage arrays that are connected directly to the host system and which guarantee the highest possible availability through RAID level 6 or RAID level 6+0. Serial Attaches SCSI (SAS) systems with an intelligent mix of classic and solid state disk (SSD) based data carriers are used.
Storage Features
- Maximum file system size of 16 Terabyte per disk.
- Total capacity maximum 1 petabyte (64 x 16 terabyte).
- Extremely fast access times, high data throughput and IOPs.
- Ideal for database based applications.
- Dynamic adjustment of the volume size during operation.
- Integration into the IDNT Virtual Filesystem possible.
- Slow migration between host systems and data center locations.
- Slow recovery of data from backup archives.
- Limited possibility of simultaneous access to multiple instances.
Cluster Storage
The IDNT Cluster Storage provides cost-effective, fast and flexible network storage. This is designed redundantly and is especially suitable for large data sets.
Storage Features
- Maximum file system size of 1 petabyte per disk.
- Total capacity maximum 64 petabytes (64 x 1 petabyte).
- Fast access times due to cluster architecture.
- Ideal for storing content and archive data.
- Shared access from several instances possible.
- Rapid migration between host systems and data center locations.
- Fast recovery of data from backup archives.
- Dynamic adjustment of the volume size during operation.
- Integration into the IDNT Virtual Filesystem possible.
- Lower data throughput and IOPs compared to local storage.
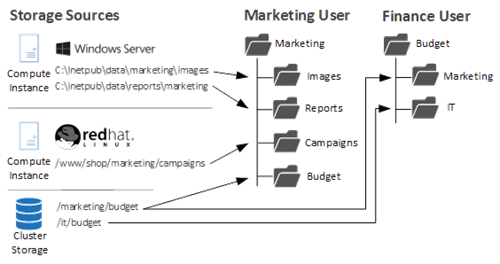
Virtual Filesystem
The IDNT Virtual Filesystem allows you to organize any directories of any system into a virtual directory tree. This means that your users no longer need to know the exact location of data, but can access the desired information in a targeted and clear manner.
SSL-Offloading
We make SSL simple and fast
When using IDNT compute instances, you can use the IDNT SSL Offloading Infrastructure. Special hardware and software takes over the encryption with the client.
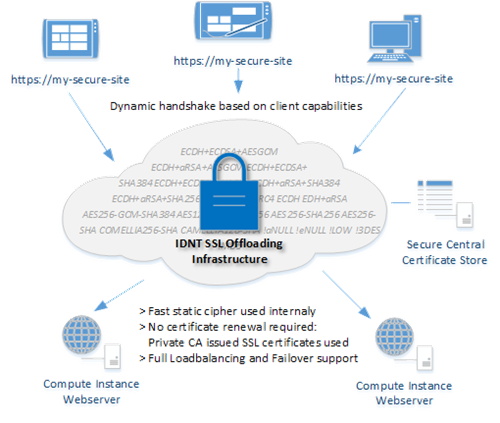
The advantages at a glance
- Reduce CPU load on your compute instances by up to 70%. They require significantly less computing power with increasing visitor numbers. There is still more budget for other tasks.
- No need to renew SSL certificates on your instances. Internal certificates are automatically issued by the IDNT Cloud Certification Authority.
- Faster connection setup for your visitors by optimizing the selection of the encryption algorithm and hardware and software specifically designed for these tasks.
- Increases the security of your application by eliminating the need to store private keys on the systems.
- Monitoring, maintenance and update of the SSL infrastructure by IDNT specialists.
- Full support of IDNT content delivery, load balancing and failover services.
Loadbalancing
Requests can be distributed to individual compute instances using various methods.
| IP-Routing | Incoming requests are distributed to individual instances at IP level according to weighting, regardless of the protocol used. The distribution is based on the source address, which means that this method can also be used with UDP connections. |
| Basic Round-Robin | Incoming requests are distributed to target instances at the IP level using the Round Robin procedure. Each time a connection is established, a new selection of a target instance occurs. |
| HTTP-Routing | HTTP requests are distributed to individual instances according to their availability and response times. Since this is done at the application level, numerous factors such as URL components or cookies for the selection of target instances can be integrated here. |
| SMTP,POP3,IMAP,FTP-Routing | As with HTTP routing, distribution is based on availability and response times. Since this is also done at application level, numerous application-specific factors can be part of the selection of the target instance. |
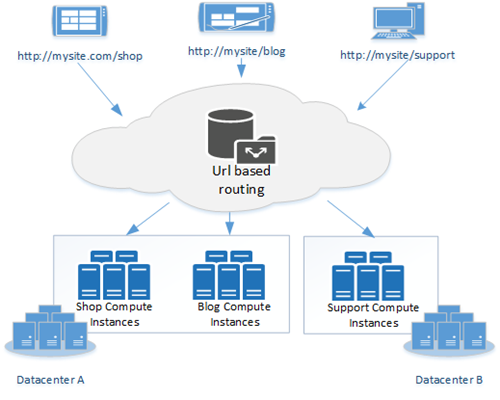
URL Routing
This is part of HTTP load balancing and enables you to create a virtual namespace, for example. Requests are distributed to one or more compute instances according to nearly freely definable rules. In addition to the url path, distribution by country of origin is also possible, similar to DNS-based routing.
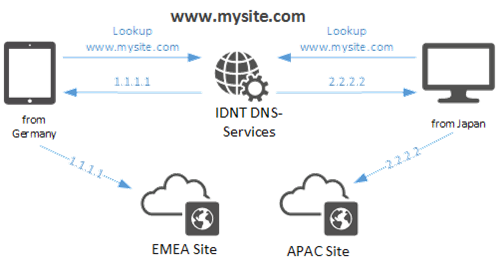
DNS Routing
DNS routing allows you to influence DNS responses based on the source address. For example, queries from Australia can be directed to a different address than those from Europe.
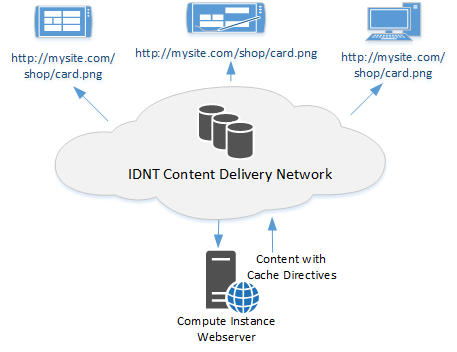
Content Delivery Optimization
The IDNT Content Delivery Network optimizes loading times for static content such as images, fonts, videos, scripts and stylesheets, which can also significantly reduce the load on your compute instance. Frequently requested content is stored directly in the working memory, which enables much faster response times and deliveries.
User Management
Our (maybe) unique user and rights management enables a detailed control of authentication, authorization and control of user logins on all compute instances and cloud services. Each instance can be assigned to a security group that can contain any number of users. Depending on the operating system, access rights can be precisely defined for each individual user or user group.
Basically, all users of the IDNT Cloud environment only need a single user account. This account can be used for all accesses and is managed by the user himself. The actual user rights are derived from the authorizations that a resource owner, such as a compute instance, grants to a user.
The IDNT user management makes teamwork particularly easy. For example, an employee of an advertising agency can use his or her personal user account to serve several customers. The only requirement is that his customer grants him access to the resources he is responsible for.
A larger infrastructure inevitably means that more users have to be connected to more services and their access to those services has to be managed. To keep this administrative effort to a minimum, users can be grouped together. In user groups identical rights can be assigned, as well as on user level. If these groups are well organized, assigning rights to employees from different departments in your company is only a matter of seconds.
Console Access
Compute instances can be accessed via SSH or Web and, in the case of Microsoft Windows, can also be accessed via Remote Desktop or Windows Power Shell. The central point of contact is the IDNT Cloud Shell, which can be used to establish connections to compute instances and services via terminals or tunnels. This makes working particularly comfortable and safe. Of course, this can also be used to transfer files via SCP or to establish a direct tunnel connection to a service such as a database.
Connection via Remote Desktop through the RDP Gateway:

Connection to the IDNT Cloud Shell via SSH:
Logon takes place using two-factor authentication and never directly to the target instance.
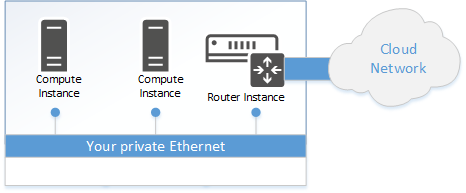
Private Networks
With IDNT compute instances, private networks at the Ethernet level can also be implemented beyond the boundaries of a data center. These represent a standard Ethernet connection, over which you can use your own protocols or IP address spaces and, for example, services such as DHCP. Using an Ethernet bridge, you can extend your intranet to systems hosted in the cloud, for example, and take over your own address space.
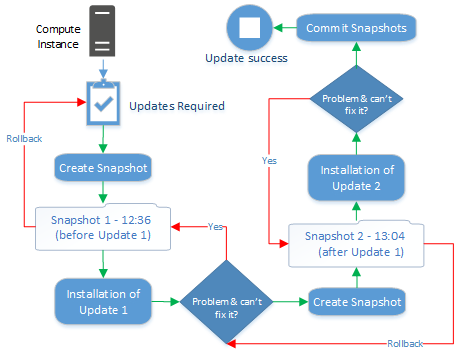
Snapshots
Snapshots are a snapshot of a compute instance to which you can return at any time. This is helpful for example for the installation of software updates, which can be reversed only with great effort. If a snapshot has been taken, you can easily return to the status before the update.